 Bob |  |  (Bob’s public key)  (Bob’s private key) |
Bob has been given two keys. One of Bob’s keys is called a Public Key, the other is called a Private Key.
| Bob’s Co-workers: | ||||
 |  |  |  |  Anyone can get Bob’s Public Key, but Bob keeps his Private Key to himself |
| Pat | Doug | Susan | ||
Bob’s Public key is available to anyone who needs it, but he keeps his Private Key to himself. Keys are used to encrypt information. Encrypting information means “scrambling it up”, so that only a person with the appropriate key can make it readable again. Either one of Bob’s two keys can encrypt data, and the other key can decrypt that data.
Susan (shown below) can encrypt a message using Bob’s Public Key. Bob uses his Private Key to decrypt the message. Any of Bob’s coworkers might have access to the message Susan encrypted, but without Bob’s Private Key, the data is worthless.
 |  | “Hey Bob, how about lunch at Taco Bell. I hear they have free refills!” |  | HNFmsEm6Un BejhhyCGKOK JUxhiygSBCEiC 0QYIh/Hn3xgiK BcyLK1UcYiY lxx2lCFHDC/A |
 |  | HNFmsEm6Un BejhhyCGKOK JUxhiygSBCEiC 0QYIh/Hn3xgiK BcyLK1UcYiY lxx2lCFHDC/A |  | “Hey Bob, how about lunch at Taco Bell. I hear they have free refills!” |
With his private key and the right software, Bob can put digital signatures on documents and other data. A digital signature is a “stamp” Bob places on the data which is unique to Bob, and is very difficult to forge. In addition, the signature assures that any changes made to the data that has been signed can not go undetected.
 |  |  |
 | To sign a document, Bob’s software will crunch down the data into just a few lines by a process called “hashing”. These few lines are called a message digest. (It is not possible to change a message digest back into the original data from which it was created.) |
 |  |  |
Bob’s software then encrypts the message digest with his private key. The result is the digital signature.
 |  |  |
Finally, Bob’s software appends the digital signature to document. All of the data that was hashed has been signed.
 |  |  |
 |  |
Bob now passes the document on to Pat.
 | First, Pat’s software decrypts the signature (using Bob’s public key) changing it back into a message digest. If this worked, then it proves that Bob signed the document, because only Bob has his private key. Pat’s software then hashes the document data into a message digest. If the message digest is the same as the message digest created when the signature was decrypted, then Pat knows that the signed data has not been changed. |
 | Doug (our disgruntled employee) wishes to deceive Pat. Doug makes sure that Pat receives a signed message and a public key that appears to belong to Bob. Unbeknownst to Pat, Doug deceitfully sent a key pair he created using Bob’s name. Short of receiving Bob’s public key from him in person, how can Pat be sure that Bob’s public key is authentic? |
It just so happens that Susan works at the company’s certificate authority center. Susan can create a digital certificate for Bob simply by signing Bob’s public key as well as some information about Bob.
|  |   |  |  |
Now Bob’s co-workers can check Bob’s trusted certificate to make sure that his public key truly belongs to him. In fact, no one at Bob’s company accepts a signature for which there does not exist a certificate generated by Susan. This gives Susan the power to revoke signatures if private keys are compromised, or no longer needed. There are even more widely accepted certificate authorities that certify Susan.
Let’s say that Bob sends a signed document to Pat. To verify the signature on the document, Pat’s software first uses Susan’s (the certificate authority’s) public key to check the signature on Bob’s certificate. Successful de-encryption of the certificate proves that Susan created it. After the certificate is de-encrypted, Pat’s software can check if Bob is in good standing with the certificate authority and that all of the certificate information concerning Bob’s identity has not been altered.
Pat’s software then takes Bob’s public key from the certificate and uses it to check Bob’s signature. If Bob’s public key de-encrypts the signature successfully, then Pat is assured that the signature was created using Bob’s private key, for Susan has certified the matching public key. And of course, if the signature is valid, then we know that Doug didn’t try to change the signed content.
原文地址:http://www.youdzone.com/signature.html
主要内容有:对称密钥系统,非对称密钥系统,数字信封,确保信息完整性hash散列,数字签名,数字证书等
1,对称密钥系统加密和解密用同一个密钥,密钥长度较短,传输熟读较快,常常用于在建立连接后的内容加密
如下图所示;典型的算法,DES(核心思想是替换加密和转换加密),三重DES
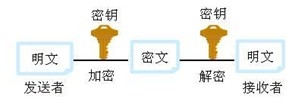
—————————————————————————————
2,非对称密钥系统,也称为公钥加密,它使用一对密钥,包括一个公钥( Public Key )和一个私钥( Private Key )。
主要作用是认证,典型有算法RSA,背包算法,如下图所示
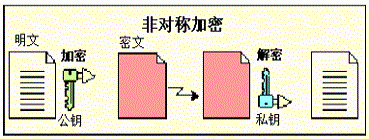
—————————————————————————————
两者常常一起使,下面是应用的案例用
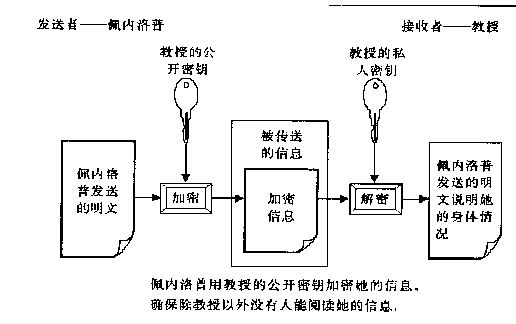
发送者公开密钥进行加密,接收者用私钥进行解密,问题是这个私钥怎么传输?
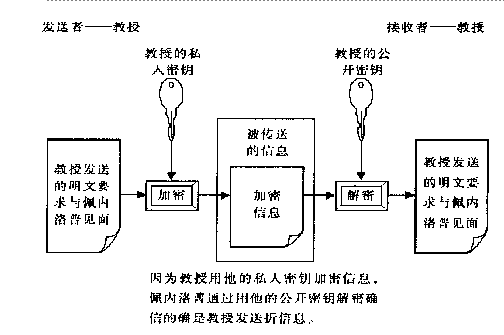
接收者用私钥进行加密,所有人都知道的公钥,安全问题?
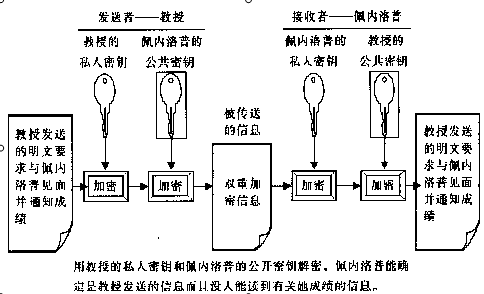
这个图片解决以上两个问题,首先用发送者的私钥进行加密,这时所有人的公钥都可以解开,然后在用接收者的公钥进行加密,
确保了只有接收者可以解开 公钥算法相对兑成算法速度较慢,无法用于加密和解密大量数据,在实际应用中常常是两者同时使用
—————————————————————————————
下面来介绍可以几个相关概念:
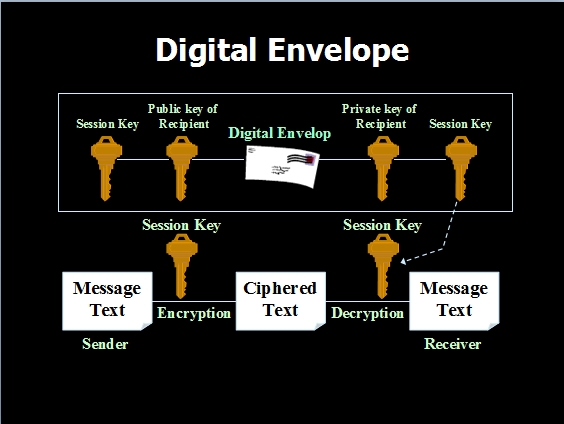
数字信封:(digitalenvelope),用公钥建立和发送一个对称密钥个给接收人,然后用这个密钥进行信息的加密和解密
通俗点将就是:通过非对称加密,获取对称加密的密钥,如下图所示:
下面来思考一个问题,当我们可以确保信息不会外泄时,我们怎么样保证所发信息的完整性?
散列值(也成哈希值),当不用个输入时,可以确保有不同的输出,通过输出值可以保证输入的唯一性
散列是一个单向的函数,即使信息有细微的变化,所输出的散列值也不同
确保信息完整的有效加密方法就是通过散列值,这点已经广泛应用,比如我们平时用的迅雷,电驴,甚至有时候在下载大型软件时,
旁边会附有他的散列值
原理如下
1.将信息和信息的散列值一同发给收件人
2.收件人收到信息,通过相同的散列算法,计算出另一个散列值
3将两个散列值进行比较,如果相同,则说明在传输过程中未出现丢失,信息是完整的
—————————————————————————————
到目前为止,我们已经解决了两个问题,即传输中信息泄露(安全性)和接收后保证信息的完整性,当我们接收到一个数
据后又是怎样确定是发送者发送的呢?下面我们来讨论这个问题 现在最关心的是发送者的身份?现实生活中我们可以使用
笔迹鉴定,按手印等,如甲在写完文章后,既按了一个手印,当乙(甚至是所有人)看到这个手印后,既可以确定是甲按的,
这个手印具有唯一性,在网络传输中我们可以将内容和这个手印一起传给接收者,当接收者看到这手印后,即认定他就是甲,
这个手印就是就是下面要讲的数据签名
—————————————————————————————
数据签名:基本原理
1.对发送者者内容进行散列

获取发送内容的哈希值,确保完整性
—————————————————————————————
2,对这个散列值进行加密(用发送者的私钥)记住一个原则,私钥加密,公钥解密不安全,但是可以用于身份验证

—————————————————————————————
3.将数字签名(用发送者私钥加密的发送内容的哈希值),附加在发送的内容中生成一个明文A,一起进行发送

—————————————————————————————
4.对明文A,用接收者的公钥进行加密生成密文B,进行发送
5.接受者在收到密文B后,用自己的私钥进行解密,还原成明文A

6.接受者从还原的明文A中,抽取中签名,然后对签名用发送者的公钥进行解密得到一个散列值F,如果能得到说明,
信息就是发送者发来的,因为发送者的私钥只有发送者的公钥能解开,至此验证了身份,对接收的明文A中内容进行
哈希散列,获取哈希D ,如果D和F一致,说明发送的是完整,
—————————————————————————————
下面我们来讨论一个更深层次的问题:在确定了发送方的身份后,我们怎么确定接收方的身份,你必须知道某人的公
钥才向他发送信息,公钥来自何处,如何确定公钥持有者的身份?
带着这个问题,我们来探究下一个话题:数字证书
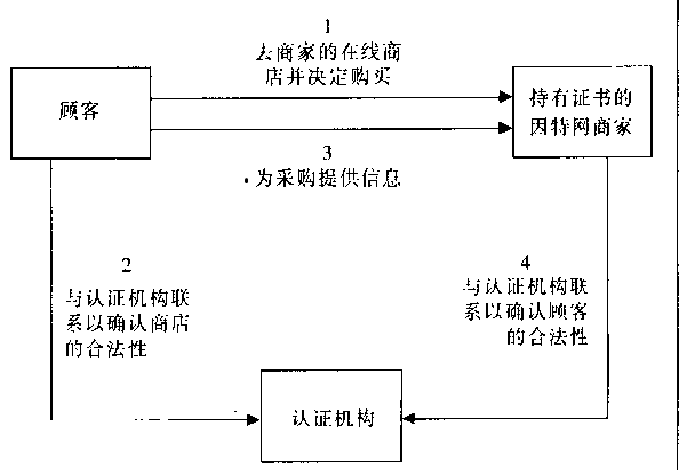
数字证书有认证中心发行,用来正式公钥和私钥持有人真实身份,个人可以像CA(认证中心)申请数字证书,这个
过程称为公钥认证,证书中心用自己 的私钥对申请人公钥和一些基本信息进行加密,寄给申请方,当有人像申请人
发送信息时,他们首先要求接收人,寄过来签名证书,然后发送人使用CA公钥给证书解密,发送人对接收人的身份
得意确认,这样最后只需要与认证方打交道即可 例子自己看看吧,我就不分析了
本文曾经出现我之前的博客中: <http://lirujia00.iteye.com/blog/1731309>
